What You Need to Know About Network Penetration Testing
Table of Contents: Net Pen Testing
- Introduction
- Importance of Penetration Testing in Cybersecurity
- Overview of Network Penetration Testing Methodologies
- Types of Penetration Testing
- Penetration Testing Process
- Tools & Techniques for Net Pen Testing
- Wireless Network Penetration Testing
- Advanced Topics in Net Pen Testing
- Resources and Further Reading
INTRODUCTION
Network penetration testing, often known as network pen testing, is a systematic process designed to identify, assess and exploit a network’s vulnerabilities and components, including servers, network services and devices. It simulates real-world attacks on a network to evaluate its security posture and resilience against cyber threats. The primary aim is to uncover weaknesses in the network’s architecture, configurations and security policies before malicious attackers can exploit them.
Objectives of Network Penetration Testing
The main objectives of conducting network penetration testing are multifaceted, focusing on identifying potential security vulnerabilities and improving network security measures. These objectives include:
- Identifying Vulnerabilities – To discover existing security weaknesses within the network infrastructure, including unpatched software, misconfigurations, weak encryption algorithms and vulnerabilities in network protocols.
- Assessing Security Posture – To evaluate the effectiveness of the current security measures and protocols. This includes testing firewalls, intrusion detection/prevention systems (IDS/IPS) and other network security controls to ensure they are properly configured and functioning as intended.
- Validating Compliance – Many industries are subject to regulatory requirements mandating regular security assessments. Network penetration testing helps organizations comply with these regulations (e.g., GDPR, HIPAA, PCI-DSS) by ensuring their networks are secure against data breaches and other security incidents.
- Prioritizing Risks – Organizations can understand the potential impact of different security weaknesses by identifying vulnerabilities and simulating attacks. This allows them to prioritize remediation efforts based on each vulnerability’s severity and potential impact.
- Enhancing Incident Response – Penetration testing can also test an organization’s incident response capabilities. Organizations can identify gaps in their incident response procedures and make necessary improvements by observing how the network and its defenders react to simulated attacks.
- Building Awareness and Training – This helps raise security awareness among IT and network administrators by demonstrating how attacks can occur and their effects. This can also serve as practical training for security teams to effectively detect, prevent and respond to malicious activities.
- Improving Security Investments – The insights gained from penetration testing can guide organizations on where to allocate their security budgets most effectively, ensuring investments are made in areas that will significantly enhance network security.
- Protecting Brand Reputation and Customer Trust – By proactively identifying and addressing vulnerabilities, organizations can prevent potential breaches that could damage their reputation and erode customer trust.
Network penetration testing is a critical component of a comprehensive cybersecurity strategy and provides actionable insights that help organizations strengthen their network security, ensure compliance with regulatory standards and protect sensitive data from cyber threats.
IMPORTANCE PENETRATION TESTING IN CYBERSECURITY
Penetration testing plays a vital role in the cybersecurity framework of organizations by proactively identifying and addressing vulnerabilities. Its importance in maintaining and enhancing the security posture of an organization’s IT infrastructure cannot be overstated. Below are key reasons that highlight the importance of penetration testing in cybersecurity:
Identifying Vulnerabilities
- Proactive Security – Penetration testing simulates cyber-attack scenarios to identify weaknesses in systems and applications before malicious actors can exploit them. It provides an opportunity to fix vulnerabilities before they become known to attackers.
- Comprehensive Assessment – Unlike automated vulnerability scans, penetration tests involve human creativity to uncover complex security issues that automated tools might miss, including logic errors and flaws requiring chained exploits.
Validating Security Controls
- Testing Defenses – Penetration testing evaluates the effectiveness of an organization’s security measures, including firewalls, intrusion detection systems and anti-virus software. It helps confirm whether these controls are correctly configured and are effective against attacks.
- Policy and Compliance – It ensures security policies are properly implemented and assists organizations in complying with regulatory requirements, reducing the risk of legal penalties for non-compliance.
Managing Risks
- Prioritizing Risks -Penetration tests help organizations understand the potential impact of different vulnerabilities, allowing them to prioritize remediation efforts based on the severity of risks.
- Resource Allocation – By identifying critical vulnerabilities, organizations can make informed decisions about allocating their resources efficiently, focusing on areas that significantly improve their security posture.
Enhancing Security Awareness and Training
- Staff Training – Penetration testing provides real-world examples of how breaches can occur, serving as an effective training tool for security teams and staff. It helps in developing a security-aware culture within the organization.
- Testing Incident Response – It also tests the organization’s incident response capabilities, ensuring that the response is swift and effective in the event of an actual breach.
Building Trust and Confidence
- Customer Assurance – Demonstrating a commitment to security through regular penetration testing can build trust with customers, partners and stakeholders, reassuring them that their data is protected.
- Competitive Advantage – In industries where security is a significant concern, a strong security posture achieved through regular penetration testing can serve as a competitive differentiator.
Continuous Improvement
- Adapting to Evolving Threats – The cybersecurity landscape constantly changes, with new vulnerabilities and attack techniques emerging regularly. Penetration testing helps organizations adapt their defenses to evolving threats.
- Feedback for Development – For software developers, penetration testing provides invaluable feedback to improve application security features, promoting secure coding practices.
Penetration testing is important to a robust cybersecurity strategy. It helps identify and mitigate vulnerabilities and plays a significant role in risk management, compliance and fostering a culture of security awareness throughout the organization. By regularly conducting penetration tests, organizations can enhance their defense mechanisms against cyber threats, ultimately protecting their assets, data, and reputation.
OVERVIEW OF NETWORK TESTING METHODOLOGIES
Network penetration testing methodologies provide structured approaches for conducting tests to identify and exploit vulnerabilities in network systems. These methodologies ensure that the penetration testing is thorough, consistent and covers all critical aspects of network security. While various methodologies exist, they generally share common phases, including planning, reconnaissance, scanning, exploitation, post-exploitation and reporting. Below is an overview of several widely recognized network penetration testing methodologies:
Open Source Security Testing Methodology Manual (OSSTMM)
The OSSTMM is a comprehensive manual offering a detailed approach to testing the security of information systems and networks. It focuses on the integrity, control and confidentiality of information, assuming attackers have any prior knowledge of the system.
Key Features:
- Provides a scientific methodology for the accurate assessment of network security.
- Emphasizes the importance of metrics in security testing to measure operational security and compliance.
Penetration Testing Execution Standard (PTES)
PTES provides a baseline standard for performing penetration tests that simulate real-world attack scenarios. It outlines seven key phases of penetration testing, from pre-engagement interactions to reporting.
Key Features:
- Covers everything from initial communication and agreement to threat modeling and vulnerability analysis.
- Aims to standardize the penetration testing process to ensure consistency and comprehensiveness in security testing.
Information Systems Security Assessment Framework (ISSAF)
The ISSAF seeks to integrate business processes with technical strategies to assess an organization’s information system security effectively. It offers detailed guidelines for each phase of the penetration testing process.
Key Features:
- Comprehensive coverage of different security domains, including network security, wireless security and application security.
- Provides best practices for security assessment and penetration testing to enhance the security posture of organizations.
NIST Special Publication 800-115
This guide from the National Institute of Standards and Technology (NIST) offers technical guidelines for conducting information security testing and assessment, including network penetration testing.
Key Features:
- Focuses on planning and conducting security assessments to identify vulnerabilities and weaknesses.
- Recommends approaches for testing, analyzing and reporting findings to improve network security.
Source: OODA Loop
Technical Guide to Information Security Testing and Assessment (OWASP)
While primarily known for web application security, the Open Web Application Security Project (OWASP) also provides network penetration testing resources within its broader information security framework.
Key Features:
- Includes methodologies for identifying and exploiting vulnerabilities in web applications and networks.
- It offers an open community and comprehensive resources for security professionals to share findings and techniques.
Choosing the right methodology depends on the organization’s specific needs, regulatory requirements and the complexity of its network infrastructure. A comprehensive approach, often integrating elements from multiple methodologies, ensures a thorough assessment and enhancement of the network’s security posture.
TYPES OF PENETRATION TESTING
Penetration testing is a critical exercise in cybersecurity, aiming to identify and mitigate vulnerabilities within network systems and applications. It simulates real-world attacks to test the resilience of IT infrastructure against security breaches. There are three primary types of penetration testing, each with unique methodologies and objectives: Black Box Testing, White Box Testing and Grey Box Testing. Understanding these types helps organizations choose the most effective approach to secure their digital assets.
- Black Box Testing – This is an approach where the penetration tester has no prior knowledge of the target system’s internal workings. The tester interacts with the system’s external interfaces, such as web applications or network protocols, to identify potential vulnerabilities and security weaknesses. It begins with minimal information about the system, typically only the name of the target company or the URL of an application. Focuses only on externally visible systems, services and applications. Utilizes automated scanning tools and manual techniques to discover vulnerabilities that can be exploited from outside the organization.
- White Box Testing – Also known as clear box or glass box testing, provides the tester with complete knowledge of the infrastructure, including network maps, source code and credentials. This approach aims to conduct a thorough examination of internal systems and logic. Testers use detailed documentation and access rights to inspect the network’s internal architecture and application code. The approach emphasizes a comprehensive assessment, including code review, to identify vulnerabilities that are not visible from the outside. Finally, it involves both automated tools and manual review to analyze the security of the code and system configurations.
- Grey Box Testing – It is a hybrid approach offering a partial knowledge of the system’s internal workings, blending elements of black box and white box testing. Testers might be given limited system information, such as architecture diagrams or some level of authenticated access, but not the full details. Testers start with an intermediate understanding of the system’s internal structures. Where possible, combine external testing of the application interfaces with internal testing of code and infrastructure. There is a focus on identifying vulnerabilities that could be exploited through partial knowledge or authenticated access.
Each type of penetration testing serves a specific purpose and offers unique insights into the security posture of an organization’s IT environment. By understanding and deploying these different approaches, organizations can comprehensively evaluate their cybersecurity defenses.
PENETRATION TESTING PROCESS
Building upon the previous definition and benefits, let’s delve deeper into the individual stages of a network penetration testing process:
Planning and Scoping
This initial phase establishes the groundwork for the entire engagement. This involves clearly defining the goals of the pen test, such as identifying specific vulnerabilities, assessing overall security posture or focusing on compliance requirements and determining the scope of the test, including the target systems and networks to be tested, authorized testing methods and the timeframe for the engagement and finally, obtaining necessary approvals from relevant stakeholders within the organization.
Identifying Critical Assets and Systems
This step involves prioritizing the most sensitive and business-critical assets within the network. These assets may include servers containing sensitive data, financial transaction systems, proprietary intellectual property databases and mission-critical infrastructure components.
Reconnaissance
Ethical hackers gather information about the target network using various techniques, which may include:
- Open-source intelligence (OSINT): Collecting publicly available information about the organization, its network infrastructure, and potential vulnerabilities.
- Scanning and enumeration: Utilizing specialized tools to discover network devices, services, operating systems, and user accounts.
- Social engineering: Ethical techniques to gather information from employees or external sources without compromising privacy.
Source: SANS Institute
Identifying Potential Entry Points and Vulnerabilities
Based on the gathered information, pen testers analyze the network to identify potential weaknesses that attackers could exploit, such as unpatched software vulnerabilities, weak or misconfigured network security settings, unsecured user accounts and inadequate access controls for sensitive systems.
Enumeration
This stage involves creating a detailed inventory of the network, including mapping all devices connected to the network, determining the operating systems on each device, identifying user accounts and privileges and understanding how the topology and different components are interconnected.
Exploitation
This is the phase where pen testers leverage their expertise and tools to simulate real-world attack techniques, gain unauthored access and assess the severity and impact of each successfully exploited vulnerability.
Post Exploitation
Once initial access is gained pen testers may maintain persistence with the network to understand how attackers might establish a foothold, move laterally to access other systems, simulate additional attack activities and evaluate the potential impact on operations and date.
Reporting & Remediation
Pen tests will document findings and prepare a list of recommendations. The comprehensive report may include information on the test scope, identified vulnerabilities and weaknesses, the potential impact of each and outline the remediation steps that should be considered. It is important to note that pen testers will work closely with clients to develop a remediation plan, prioritize efforts and then verify the effectiveness of each.
TOOLS AND TECHNIQUES FOR NET PEN TESTING
Network penetration testing requires a blend of sophisticated tools and techniques to effectively identify and exploit vulnerabilities within a network. This arsenal includes both off-the-shelf software and custom scripts designed to probe deeply into the network’s defenses. Moreover, ethical and legal considerations play a critical role in guiding how these tools and techniques are employed. Below is an overview of the tools and techniques integral to network penetration testing, highlighting popular tools, the role of custom scripts and the ethical/legal landscape.
Popular Penetration Testing Tools
- Nmap (Network Mapper) – Nmap is a free and open-source utility for network discovery and security auditing. It is used to discover hosts and services on a computer network, thus building a “map” of the network. It helps identify open ports, running services, and the type of devices connected to the network.
- Metasploit Framework – The framework is a powerful tool for developing and executing exploit code against a remote target machine. It contains a suite of tools allowing the user to create and manage exploits, payloads and other attack tools.
- Wireshark – It is a network protocol analyzer that lets you capture and interactively browse the traffic running on a computer network. It provides deep visibility into the network’s operations, making it an invaluable tool for troubleshooting and analyzing security issues.
Custom Scripts and Toolkits
- Custom Scripts – Penetration testers often develop their own scripts to automate the exploitation of specific vulnerabilities or to parse through data in a manner tailored to their unique objectives. Languages such as Python, Bash and PowerShell are commonly used for scripting in penetration tests.
- Toolkits – Beyond individual scripts, testers may assemble toolkits—a collection of scripts, tools and software—customized for specific testing scenarios or objectives. These toolkits can be adjusted for the particularities of each engagement, providing flexibility and efficiency.
Ethical and Legal Considerations in Tool Usage
- Ethical Considerations – The use of penetration testing tools must adhere to strict ethical guidelines. Testers should have explicit permission from the rightful owners or managers of the systems being tested. The primary aim should be to enhance security without causing harm or disruption to the operational integrity of the target network.
- Legal Considerations – The legal framework surrounding penetration testing varies by country and jurisdiction. It’s important to ensure all testing activities are within legal boundaries, with appropriate permissions and contracts in place. Unauthorized use of these tools can be considered illegal hacking and lead to serious legal consequences.
- Confidentiality and Integrity – Maintaining the confidentiality and integrity of the data encountered during penetration testing is paramount. Testers should ensure that sensitive information is securely handled and that their activities do not inadvertently compromise the data or the network’s functionality.
Network penetration testing is a sophisticated discipline that relies on a combination of advanced tools, custom scripts and meticulous planning.
The ethical and legal considerations surrounding these activities underscore the responsibility that comes with possessing the capability to probe and potentially exploit network vulnerabilities. By adhering to these principles, penetration testers can help secure networks against threats while maintaining the trust of those whose systems are being tested.
WIRELESS NETWORK PENETRATION TESTING
Wireless networks have become ubiquitous, providing convenient access to the internet from anywhere within their range. However, this convenience comes with its own set of security challenges and vulnerabilities that need to be managed to protect data and maintain a secure network environment. Understanding these challenges, identifying specific vulnerabilities, using appropriate tools for penetration testing and applying effective mitigation strategies are crucial steps in securing wireless networks.
Introduction to Wireless Network Security Challenges
Wireless networks, by their nature, broadcast data through the air, making them inherently more susceptible to eavesdropping and unauthorized access than wired networks. The key security challenges include:
- Eavesdropping – Since wireless communications are broadcast through open air, they can be intercepted by unauthorized users.
- Unauthorized Access – Weaknesses in authentication mechanisms can allow attackers to connect to a network without authorization.
- Data Integrity Attacks – Attackers can capture and alter the data being transmitted over the network.
- Man-in-the-Middle Attacks (MitM) – Attackers can intercept and modify communications between two parties without their knowledge.
- Rogue Access Points – Unauthorized access points installed within the network can trick users into connecting to them, allowing attackers to monitor and capture sensitive information.
Specific Vulnerabilities Associated with Wireless Networks
Wireless networks have several specific vulnerabilities that attackers can exploit:
- Weak Encryption – Older encryption standards like Wired Equivalent Privacy (WEP) are easily broken, exposing network traffic to eavesdropping.
- Poorly Configured Access Points – Default configurations and weak passwords make access points easy targets for attackers.
- Evil Twin Attacks – Attackers set up a malicious access point with the same SSID as a legitimate one to trick users into connecting.
- Packet Injection – Attackers inject malicious packets into legitimate traffic, potentially disrupting services or exploiting vulnerabilities.
Tools and Techniques for Wireless Network Penetration Testing
Several tools and techniques are used for identifying vulnerabilities in wireless networks:
- Aircrack-ng – A suite of tools for 11 wireless network security assessments. It focuses on areas like monitoring, attacking, testing, and cracking. It can crack WEP and WPA-PSK keys after capturing enough data packets.
- Kismet – A wireless network detector, sniffer, and intrusion detection system. It works with Wi-Fi (802.11) networks but covers Bluetooth and other wireless protocols. Kismet is useful for detecting hidden networks and rogue access points.
- Wireshark (for wireless) – While Wireshark is a network protocol analyzer for wired and wireless networks, it can be particularly useful for monitoring wireless traffic and analyzing the packets for vulnerabilities.

Mitigating Risks in Wireless Networks
To mitigate the risks associated with wireless networks, consider the following strategies:
- Encryption Standards – Use strong encryption protocols like WPA2 or WPA3 to protect the data transmitted over the network. Avoid using outdated protocols like WEP.
- Secure Configuration Practices – Configure wireless access points and routers securely by changing default passwords, disabling WPS (Wi-Fi Protected Setup) and hiding SSIDs to prevent easy detection.
- Regularly Update Firmware – Keep the firmware of wireless devices updated to patch known vulnerabilities.
- Network Segmentation – Separate sensitive data and services from the main wireless network using VLANs or separate networks.
- Use VPNs – Encourage or require Virtual Private Networks (VPNs) to connect to the network remotely to ensure data is encrypted and secure.
Implementing robust security measures and regularly conducting penetration tests using specialized tools can significantly reduce the vulnerabilities associated with wireless networks, enhancing their security against potential attacks.
ADVANCED TOPICS IN NET PEN TESTING
Automated penetration testing involves using software applications to find network, system, and application vulnerabilities. These tools can quickly identify and report potential security issues, often with less time and resource investment than manual penetration testing. They are particularly effective for repetitive tasks and can cover a wide area of testing targets relatively quickly. Common automated penetration testing tools include:
- Nmap – Network mapping tool that identifies devices on a network and their vulnerabilities.
- Metasploit – A framework for developing and executing exploit code against a remote target machine.
- Burp Suite – An integrated platform for performing security testing of web applications.
- OWASP ZAP (Zed Attack Proxy) – An open-source web application security scanner.
- Nessus is a widely used vulnerability scanner for identifying software vulnerabilities and misconfigurations.
Cloud Penetration Testing Challenges and Strategies
Cloud penetration testing poses unique challenges due to the nature of cloud computing environments, including multi-tenancy, dynamic provisioning and the shared responsibility model. Key challenges include:
- Scope Definition – Clearly defining the scope of testing within a cloud environment can be complex due to the dynamic nature of cloud resources.
- Legal and Compliance Issues – Understanding and adhering to cloud providers’ policies and relevant legal regulations are crucial to avoid violations.
- Access Limitations – Limited visibility and control over the underlying infrastructure can restrict testing methods.
Strategies for overcoming these challenges include:
- Comprehensive Planning – Develop a detailed testing plan that includes scope, tools, methods and compliance considerations.
- Coordination with Cloud Providers -Engage with cloud providers to understand their penetration testing policies and gain necessary permissions.
- Using Cloud-native Tools – Leverage tools and services provided by cloud platforms designed for security assessment and monitoring within their environments.
Red Team vs. Blue Team Exercises
Red team and blue team exercises are a form of security assessment where two teams are pitted against each other to test the effectiveness of an organization’s security posture.
- Red Team – Acts as the attacker, attempting to exploit vulnerabilities and penetrate the organization’s defenses using tactics, techniques and procedures (TTPs) like those used by real-world adversaries. The goal of the red team is to identify weaknesses in security controls and operational practices.
- Blue Team – Represents the organization’s defense and is responsible for detecting, preventing and responding to the red team’s attacks. The blue team aims to improve the organization’s defensive capabilities by identifying gaps in detection and response processes.
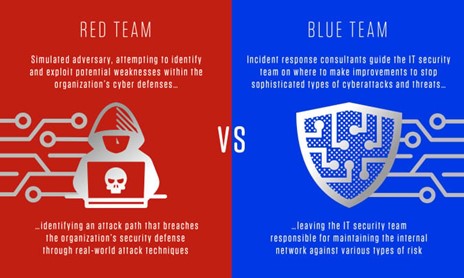
Source: CrowdStrike
The primary goal of these exercises is to provide a realistic assessment of the organization’s security defenses and incident response capabilities, allowing for identifying and remedying vulnerabilities before malicious actors can exploit them. Collaboration and after-action reviews between the red and blue teams are crucial for maximizing the benefits of these exercises, as they offer insights into improving security posture and response strategies.
RESOURCES AND FURTHER READING
The cybersecurity and penetration testing field is vast and constantly evolving, with numerous resources available for those interested in learning more or advancing their skills. Here’s a list of recommended books, online courses, certifications and communities to get you started or take you to the next level.
Books
- “The Web Application Hacker’s Handbook” by Dafydd Stuttard and Marcus Pinto – A comprehensive guide to web application security.
- “Penetration Testing: A Hands-On Introduction to Hacking” by Georgia Weidman – An excellent introduction to penetration testing.
- “Hacking: The Art of Exploitation” by Jon Erickson – Offers a deep dive into the world of hacking, from basic principles to advanced techniques.
- “Red Team Field Manual” by Ben Clark – A handy reference guide for red teamers.
- “Blue Team Handbook: Incident Response Edition” by Don Murdoch is an essential reading for anyone interested in blue team roles and incident response.

Online Courses and Certifications
- Offensive Security Certified Professional (OSCP) – One of the most respected certifications for penetration testers, focusing on hands-on offensive information security skills.
- Certified Ethical Hacker (CEH) – Offers a comprehensive ethical hacking and network security training program to meet the standards of highly skilled security professionals.
- SANS Institute Courses – Provides a variety of courses and certifications in cybersecurity, including penetration testing and ethical hacking.
- Coursera & Udemy – Both platforms offer a range of courses on cybersecurity and penetration testing for all levels, taught by industry professionals.
- Cybrary – A community-driven platform offering free and paid cybersecurity and IT courses.
These resources are just the starting point. Cybersecurity is vast, with new vulnerabilities, tools and techniques emerging regularly. Engaging with the community, continuing education and hands-on practice are key to staying current and proficient in penetration testing and cybersecurity.
Network Penetration Testing Services
Businesses face various cybersecurity challenges and maintaining network security is an essential part of a comprehensive cybersecurity plan. Adams Brown Technology Specialists has years of experience helping companies maintain a strong cybersecurity position. Our services include:
- Compliance & Regulation
- Cybersecurity
- Managed IT Services
- Penetration Testing
- SOC Reporting
- Technology Consulting
- Vulnerability Scanning
Adams Brown Technology Specialists provides network penetration testing services to companies in Atlanta (GA), Billings (MT), Boise (ID), Charleston (SC), Charlotte (NC), Cheyenne (WY), Chicago (IL), Cleveland (OH), Colby (KS), Dallas (TX), Denver (CO), Des Moines (IA), Fargo (ND), Garden City (KS), Great Bend (KS), Hays (KS), Houston (TX), Hutchinson (KS), Indianapolis (IN), Jackson (MS), Jonesboro (AR), Kansas City (KS/MO), Larned (KS), Lincoln (NE), Little Rock (AR), Los Angeles (CA), Manhattan (KS), McPherson (KS), Milwaukee (WI), Minneapolis (MN), Orlando (FL), Philadelphia (PA), Phoenix (AZ), Richmond (VA), Salt Lake City (UT), Sioux Falls (SD), St. Louis (MO), Tampa (FL), Tulsa (OK), Tucson (AZ), Western Kansas, Wichita (KS) and Wilmington (DE).
Net Pen Testing FAQs
Network penetration testing, often abbreviated to pen testing, involves simulated cyberattacks on your company’s network to help uncover potential vulnerabilities. The simulations include various techniques of attack to thoroughly search for weaknesses in the network and firewall. The test should attempt access through web applications, APIs and operating systems from both internal and external attack approaches.
Pen testing typically follows a vulnerability assessment. While vulnerability scanning is conducted using automated tools, penetration testing is performed by skilled cybersecurity professionals who take a more exhaustive and deeper dive into the network’s defenses.
There are several steps to the process, including:
- Planning and reconnaissance – The first step in network penetration testing involves planning and gathering information. Testers identify the scope and goals of the test, including the systems to be tested and the methods to be used. Reconnaissance involves collecting data about the target network, such as domain names, IP addresses and other publicly available information.
- Scanning – Once the initial information is gathered, the next step is scanning. This involves using tools to identify open ports, services running on those ports and any potential vulnerabilities. Scanning can be done both externally, from outside the network, and internally, from within the network.
- Gaining access – After identifying potential vulnerabilities, testers attempt to exploit them to gain access to the network. This can involve various techniques such as SQL injection, cross-site scripting (XSS) and phishing attacks. The goal is to see how far the tester can penetrate the network and what data can be accessed.
- Maintaining access – Once access is gained, the next step is to see if the attacker can maintain access and move laterally within the network. This phase involves using tools and techniques to remain undetected while exploring the network and gathering more information.
- Analysis and reporting – After the testing is complete, the results are analyzed. This includes identifying which vulnerabilities were exploited, what data was accessed and how long the tester was able to maintain access without detection. A detailed report is then created, outlining the vulnerabilities found, the methods used to exploit them and recommendations for remediation.
This testing is important for a variety of reasons, including:
- Education – A penetration test can educate an organization in several ways ultimately helping to strengthen its cybersecurity posture, build awareness and guide strategic investments. Specifically, penetration testing:
- Reveals real world vulnerabilities – Penetration tests simulate real-world cyberattacks, revealing technical weaknesses that might otherwise go unnoticed. In doing so, pen tests not only expose these vulnerabilities but also demonstrate the potential consequences if exploited. It will show how an attacker could move through your systems, access sensitive data or disrupt operations.
- Provides a benchmark for continuous improvement – Penetration tests offer a clear benchmark for measuring your organization’s security maturity over time, so you can track progress and identify areas for investment. The insights gained also drive meaningful improvements in policies and internal processes ultimately ensuring that security measures evolve alongside emerging threats and operational needs.
- Data protection – Aside from a myriad of data privacy laws you should always be compliant with, even the smallest of breaches could damage your relationship and trust with your clients.
- The modern consumer is more internet-savvy than ever before. They are more aware of how their information is used by businesses like Google or Apple, for example. Expectations for how their data is protected and their real perception of how data is protected are two very different things. This is a great opportunity for you and your company to build trusting, long-standing relationships with your clients by ensuring the data that you collect and retain is vigilantly protected and secure.
- Financial loss – IBM reported the average price of a data break in 2023 was $4.45 million, which is a 15% increase over the previous three years. One singular data breach can demolish a company’s bottom line and cause it to permanently close its doors. Cybercriminals try to stay ahead of the game with tech-savviness and clever approaches. These consequences can include permanent destruction of data, a halt in productivity, theft of intellectual property, fraud, embezzlement and damage to your company’s reputation.
- External network pen testing (black box) simulates an outsider attack with no internal knowledge specifically targeting public-facing assets like firewalls, web servers and exposed IPs. The goal is to test your perimeter defenses just like a real-world hacker would.
- Internal network pen testing (gray box) assumes the attacker is already inside and mimics insider threats or post-breach scenarios. It evaluates risks like lateral movement, privilege escalation and access to sensitive systems across the internal environment.
- Wireless pen testing targets Wi-Fi infrastructure by testing encryption standards (WPA2/WPA3), rogue access points, weak passwords and misconfigurations. This type of testing helps secure the airspace around your offices and facilities.
- Social engineering pen testing (red team tactics) puts the human firewall to the test. Using phishing, pretexting, baiting or tailgating, this approach evaluates how susceptible your employees are to manipulation and how well your cybersecurity training and protocols hold up under real pressure.
- Physical security pen testing assesses the effectiveness of an organization’s physical barriers and procedures. Testers attempt badge cloning, lockpicking or even plugging into open network jacks. This type of testing is ideal for facilities with high security requirements.
- Cloud pen testing examines cloud environments like AWS, Azure, or GCP for misconfigured storage, open ports, weak IAM roles, and exposed services—everything from S3 buckets to serverless functions.
- IoT/OT network penetration testing targets Internet of Things (IoT) or Operational Technology (OT) networks used in manufacturing, energy, healthcare and other industries. This type of penetration testing often uncovers outdated firmware, legacy protocols and exploitable gaps in device-to-network communication.
Penetration tests can be designed in different ways and should be constructed to take the unique features of your network into account. If the test is well-designed, a penetration test report will clearly explain how the tester obtained entry to your network and how they were able to take over your server and/or computers. The penetration test report gives context and explanation to the vulnerabilities that have been identified.
With a blueprint that shows how to remediate the risk and prevent an attacker from getting to the servers, most business owners are able to move forward with confidence and a reasonable, actionable budget for ongoing security measures.
Sometimes security measures must be geared to current high-profile threats that have cropped up in the marketplace. But that depends on the type of business, the data that may be at vulnerable and the risk appetite of the business owner. All IT security upgrades come with a price tag, and priority should be given to the vulnerabilities and threats that are most likely to affect your organization.
As cybersecurity threats continue to grow, most organizations should consider including penetration testing in their regular IT security protocols. Penetration testing goes hand-in-hand with vulnerability scanning, but these tools differ and are most effective when used together to provide a detailed picture of an organization’s cybersecurity risk profile.
Though they should be part of every organization’s cybersecurity management plan, vulnerability scanning and penetration testing are not widely practiced today except in regulated industries where such measures are required.
Vulnerability scans examine your IT network – including hardware and software – and identify any areas that are vulnerable to attack. The reports are often long and highly technical, so the prospect of shoring up the system can seem overwhelming.
Penetration testing reveals how a hacker could actually get into your system through one of those vulnerabilities. This can help prioritize which vulnerable areas of your system should be addressed first. The penetration test gives you a real-world picture of what a hacker could do, what data they could access and how you would be impacted.
Think of it like protecting your house. A vulnerability scan may show that all your doors and windows have weak or missing locks, and your basement bulkhead doesn’t lock at all. A penetration test would simulate an actual break-in, potentially showing that the first-floor windows are the most likely point of entry for a criminal. The results of the penetration test would reveal that installing new window locks on the first floor would be the most effective immediate measure to secure your home while strengthening the security on your doors and basement bulkhead might be next.
National standards on vulnerability scanning and penetration testing are defined by several organizations such as the nonprofit Center for Internet Security (CIS) and the Cybersecurity & Infrastructure Security Agency (CISA), an agency within the U.S. Department of Homeland Security. However, none of these standards are required or enforced, and organizations should determine frequency based on several factors:
- Industry – Does your business operate in an industry that collects substantial personal data from customers, such as healthcare or financial services? Or do you have hundreds or thousands of employees whose personal information is contained in human resources files?
- Volume of data – Does your organization process high volumes of data every day, and do you practice good data protection measures such as daily backups?
- Risk – Is your industry a frequent target of cyberattacks?
Generally, a mid-sized company should do vulnerability scanning at least once per quarter, and a penetration test every year. That’s a starting point that will provide a roadmap to security upgrades that can be done each quarter to continuously improve the system’s safeguards. Each quarterly scan will verify the effectiveness of the improvements made since the last quarter.
After the penetration test is completed, the testing team typically delivers a detailed report that outlines their findings. This report includes a high-level executive summary for non-technical stakeholders, as well as a technical breakdown of vulnerabilities discovered, their severity, how they were found and steps for remediation. The organization’s internal IT or security team should carefully review this report, assess the risk each issue presents and begin prioritizing fixes based on severity and potential business impact.
A debrief session is often scheduled with the penetration testers to walk through the findings, clarify any technical details and answer questions. The organization may also initiate internal reviews to determine why certain vulnerabilities existed and whether additional controls or policies need to be introduced. If significant changes or fixes are implemented, a retest may be scheduled to verify that the vulnerabilities have been properly resolved. The ultimate goal is to use the results of the test to strengthen the organization’s overall security posture and reduce future risk.

